blogx
netlogx’ Fundraiser Drives Positive Change that is Personal
The Wellness Committee of netlogx, a company that aids governments and businesses in solving operational challenges and operating more effectively with project management, helped raise over $1000 and collectively walked over four million steps during Pancreatic Cancer Awareness Month in November 2024 during a campaign to honor the life and legacy of its co-founder Nick Taylor, who passed away from the disease the previous year.
Turning Hardship Into Opportunity
My spouse inspires me every day, but this year, it was her diligence to radically change our eating habits, walking every day despite the Minnesota weather extremes, and finding new recipes that made us feel nourished that was especially inspiring to me.
Why My Grandchildren Are My Greatest Inspiration
There is something special about becoming a grandparent that words can barely describe.
Three Cities, Endless Inspiration
When I think of all the experiences I had over the course of 2024, several memories stand out that are all linked by the same theme…travel. Over this past year, I had the privilege of visiting three (3) different countries, all of which offered different and exciting...
Inspiration through Solitude: Alone but not Afraid
My favorite TV show is “Alone.” For those unfamiliar, it’s a survival show where 10 contestants are dropped off into an isolated location with ten items of their choosing and are tasked with surviving on their own in the wilderness.
Finding Strength: Navigating Loss and Discovering Resilience
Losing a loved one is unquestionably one of life’s greatest challenges, in particular when it happens suddenly or unexpectedly.
Readiness Assessments—are you ready to implement change?
Is it human nature to resist change? We often deviate from change due to the fear of failure and the unknown, even if those changes are inevitable and ultimately lead us to success.
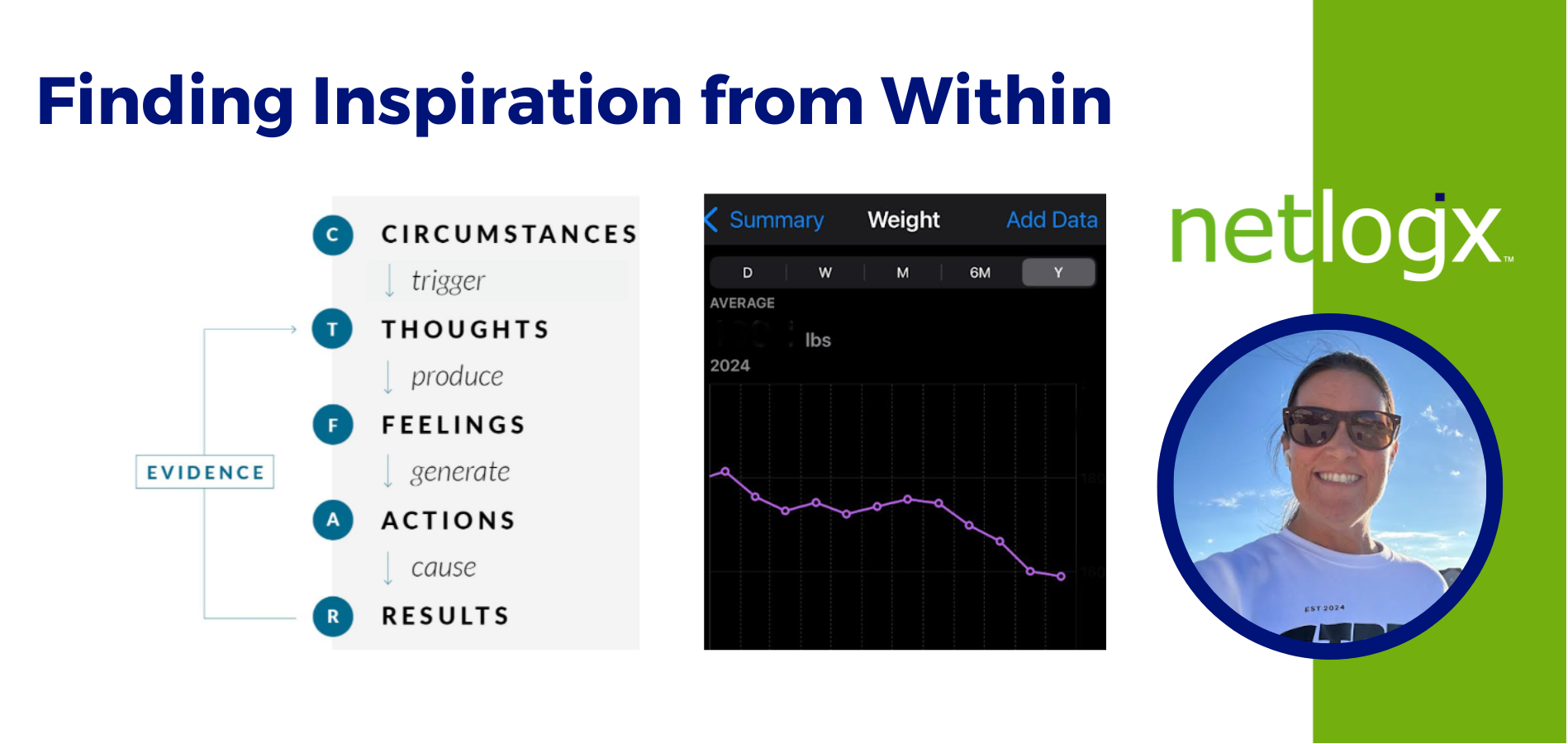
Finding Inspiration from Within
The word Inspiration has always made me think of a person who has overcome extreme difficulties to achieve what feels impossible or from a very challenging circumstance.
The Internet Can Inspire
“Inspiration is a feeling of enthusiasm you get from someone or something that gives you new and creative ideas,” as defined in the Oxford Dictionary. As I focus on this, I am reminded of the people in my life who I am inspired by on a daily basis. This may surprise...
How to Identify Functional and Technical Requirements for Future-State Success
At netlogx, our team works with various government organizations at the local and state level, offering reliable solutions for various challenges—especially as it relates to large-scale system changes.
netlogx’ Beth Clark Named Member of the Board for WIPP Education Institute (WEI)
Beth Clark, a business development consultant for netlogx, a company that aids governments and businesses in solving operational challenges and operating more effectively with project management, business process consulting, and strategic consulting services, was recently named a member of the Board of Directors to the WIPP Education Institute (WEI) and began serving a three-year term in Oct. 2024.
How Simple Lifestyle Changes Can Improve Your Quality of Sleep
Over the past two years, I’ve been on a bad trend of staying up too late into the night. I’d scroll on my phone or would spend my time worrying about whatever the next day’s tasks were.
Let’s Partner
netlogx has a proven track record of aiding governments and businesses with strategic, hands-on support to bring projects to successful completion. Contact us to learn more about our capabilities and how we can support your organization.